As Communications Service Providers (CSPs) worldwide scale up the deployments of their 5G networks, they face strong pressure to optimize their Return on Investment (RoI), given the massive expenses they already incurred to acquire spectrum as well as the ongoing costs of infrastructure rollouts.
Security Prevention Alone Is Not Enough
Security prevention has been the predominant philosophy guiding security solutions to date. The premise is that it is possible through defense in depth and multiple layers of security to foil attacks from the outside. In other words, by building higher and thicker walls of defense, we can keep the enemy out. But, if history teaches us anything, it’s that a strategy based on defensive walls alone will not succeed. As a case in point, let’s look at the Maginot Line.
1. SECURITY PREVENTION IS A MAGINOT LINE OF DEFENSE
After the First World War, France built the Maginot Line, a line of concrete fortifications that stretched from Switzerland to Belgium. It was hailed by experts as a work of genius as it was impervious to bombardment from land or air and allowed the French time to mobilize in the event of an attack. After the years of defensive trench warfare of the First World War, one would be forgiven for assuming that any future confrontations would be a “guerre de longue durée” or “war of long duration”. In other words, the Maginot Line made sense.
Nevertheless, the Maginot Line had its weaknesses. It did not extend along the Belgian border for fear of offending Belgium. The plan here was to concentrate troops and repel an invasion from Belgium. But, the assumption was that a German invasion could not be directed through the Ardennes Forest just north of the wall so this part of the line was not defended. As we all now know, this is exactly where the Germans struck and the rest, as they say, is history.
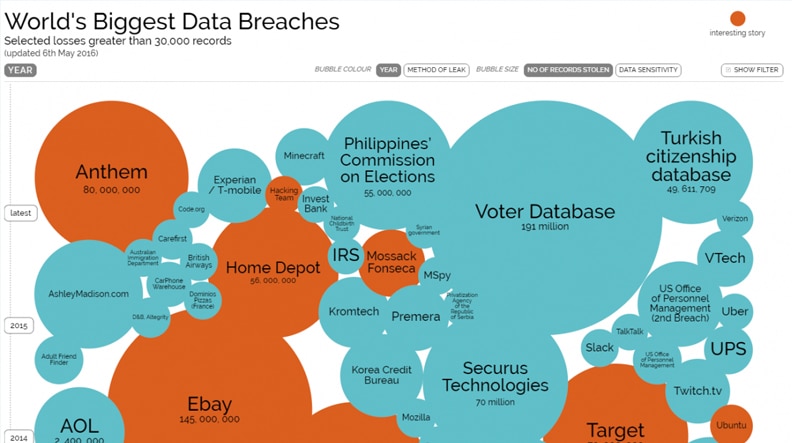
In many ways, this story reflects the current situation with network security. Our “Maginot Lines” of security prevention are actually being surmounted every day – we just don’t always know it! If you want evidence to this fact, just see this fascinating interactive graphic history of the largest security breaches of the last decade:
http://www.informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/


Source: The Ponemon Institute “The Cost of Malware Containment”, January 2015
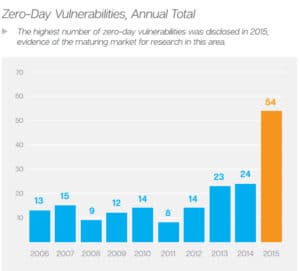
The number of “zero-day-threats”, which are new security threats that have never seen before, has also increased dramatically over the last year from 24 in 2014 to 54 in 2015, according to Symantec’s Internet Security Threat Report.
Zero-day-threats are a problem as current security prevention techniques are based on databases of known threats. If the threat is not known, then the security prevention solutions are powerless. The attacker is virtually invisible and blends in with the crowd.


Source: Symantec Internet Security Threat Report, Volume 21, April 2016
2. THE INTERNAL NETWORK IS THE ARDENNES FOREST OF SECURITY
The ingenuity and daring that the Germans showed in attacking through the Ardennes, which was believed to be impossible and thus not defended, is synonymous with the daring and ingenuity that cyber criminals show every day in identifying weaknesses in security defenses.
The “Ardennes Forest” of security today is the internal network. Up until recently, it was assumed that all attacks started from outside the perimeter of our defenses, but with the advent of Bring Your Own Devices (BYOD), larger USBs and malicious behavior by employees, the internal network has become vulnerable to attacks from within.
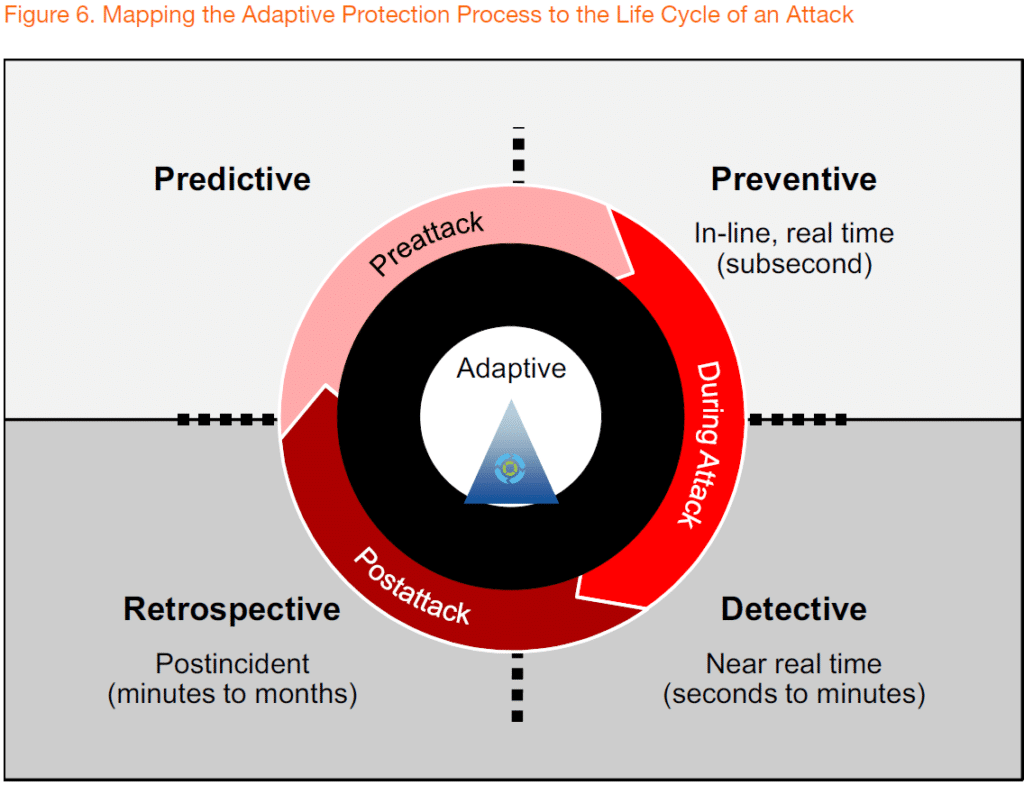
The combination of zero-day-threats and attacks from within the internal network are now driving new types of solutions referred to as “Advanced Threat Detection”. These security detection solutions focus on detecting anomalous behavior in the network itself so that potential threats can be identified and dealt with before they cause damage. These are not a replacement for security prevention, but a complement, as this graphic outlining the Gartner “Adaptive Protection Process” shows:


Source: Gartner “Designing an Adaptive Security Architecture for Protection from Advanced Attacks”, January 2016
Both preventive and detective solutions are needed to counteract attacks, but the information gathered by both can be used in retrospective analysis, to determine if any further measures need to be taken and to learn from experiences.
This is the basis for increased interest in security detection solutions and in “Designing an Adaptive Security Architecture for Protection from Advanced Attacks”, Gartner estimates that the current 20% share of security spending on security detection solutions will rise to 60% by 2020. This also explains recent acquisitions by major security vendors, such as BlueCoat’s acquisition of Solera, RSA’s acquisition of NetWitness and Cisco’s acquisition of both SourceFire and Lancope.
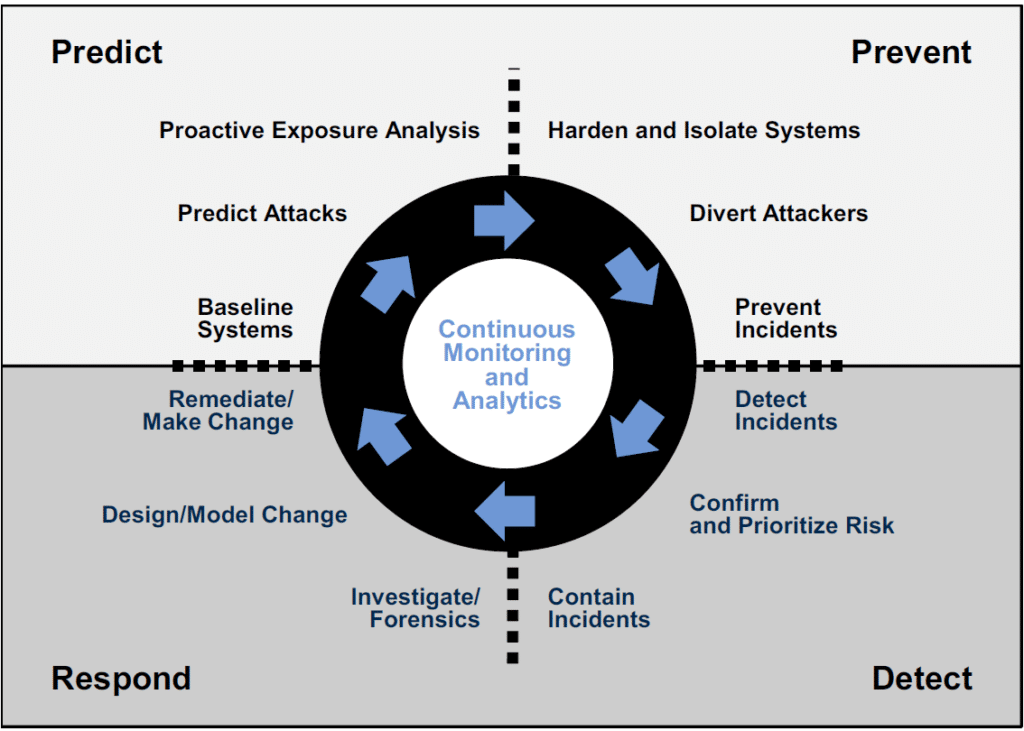
The corner stone of security detection solutions is continuous monitoring and analytics:


Source: Gartner “Designing an Adaptive Security Architecture for Protection from Advanced Attacks”, January 2016
This includes not just monitoring of logs and Netflow information, but also real-time packet capture and analysis, as well as recording of packet capture data for near-real-time and post-analysis. By analyzing data traffic, it is possible to build a profile of normal network behavior that can then be compared against real-time data or recorded data to detect if something out-of-the-ordinary is occurring.
3. THE DELUGE OF SECURITY ALERTS IS THE HOLE IN THE WALL
The alert of potential malicious behavior can be compared against information from security prevention solutions to assess if an attack is underway. Conversely, it can be used to validate a threat alert from a security prevention solution that could be a “false positive”. In either case, there is great value in using this information to verify what is happening.In a report entitled “The Cost of Malware Containment” from January 2015, the Ponemon Institute estimated that in a typical week an organization can receive up to 17,000 malware alerts. There are not enough resources to respond to each of these alerts and the cost of responding is also significant. The average cost of time wasted responding to inaccurate and erroneous intelligence was estimated by Ponemon Institute to be up to $1.27 million annually for a typical organization.
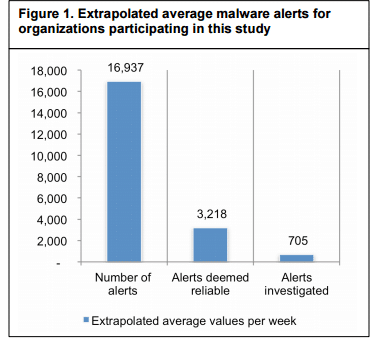
Because of this, only 4% of all malware alerts are investigated. The Ponemon Institute also found that their prevention tools miss 40% of malware infections in a typical week! The longer this goes undetected, the larger the potential risk of a breach. This is the hole in the security wall that many attackers exploit.
So, the solution is not just about more alerts from security detective appliances, but also automation of tools that can correlate information from multiple sources in order to determine the real situation, but also have the capacity to examine each and every alert. This requires big data analysis, machine learning and artificial intelligence solutions, topic covered in a previous blog:
http://www.napatech.com/artificial-or-not-the-intelligence-is-here/.
With automated tools, you get the full benefit of combining intelligence from preventive and detective solutions to form a security solution that increases your success rate in detecting and prevents a security breach, while also making a better use of your precious security staff who are currently overwhelmed.
4. EFFECTIVE DEFENSE COMBINES PREVENTION AND DETECTION
So, as we can see, higher and thicker security prevention perimeters provide a false sense of security, if you pardon the pun! These are the Maginot Lines, which lull us into the disbelief that we are safe. But, as we have seen above, these defenses are breached every day, to an extent that security professionals can’t keep up.
By augmenting security prevention with security detection solutions based on continuous monitoring of the network with packet capture and capture-to-disk solutions, it is possible to detect threats that have not been caught by security prevention solutions. By combining this with automated tools capable of correlating data from both prevention and detection tools, we can help security professionals deal with the growing deluge of security alert information and build a reliable threat intelligence platform for predicting future security breaches.
The Maginot Line was once considered a work of genius, but, after the Second World War, became the butt of many jokes, such as the Maginot Line is French for “speed bump ahead”. If you don’t want your network security to become a joke, then invest in security detection, continuous monitoring and automated tools for correlation of data alerts.